Steven Vona is a Linux administrator whose passion for technology extends beyond the day to day and into a love of teaching his skills to others. Steven is trained and certified in multiple technologies, including Microsoft Windows, Linux, VMWare and Cybersecurity, and has over 16 years of experience working in both the public and private sectors. Because Steven did not complete a traditional educational path, he is mostly self-taught and a strong believer in learning by experimentation. Steven began to teach himself programming at age 12 and ran a BBS in 1988; when teaching, he encourages others to try different solutions and learn from their mistakes and successes. Outside of technology, Steven is an animal lover and an avid photographer who enjoys exploring and photographing his native city, Philadelphia.
Steven Vona
How to Set the http_proxy Variable in Linux
View and Edit EXIF Data from Images on Linux Command Line
Force User to Change Password Upon Next Login
How To Grep Out Blank Lines In A Text File
Creating IPsec Tunnel Between Two Hosts using openswan
Configuring Transaction Signatures (TSIG) on BIND 9
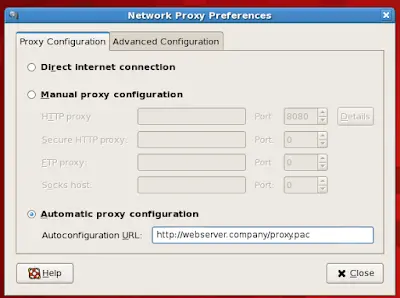
How to configure system proxy settings in Red Hat Enterprise Linux
Block Unwanted Advertisements with a Hosts File on Linux
Extract a Single File From a tar Archive
Grep All Email Addresses from a Text File
Join Our Newsletter
Categories
- Bash Scripting (17)
- Basic Commands (51)
- Featured (7)
- Just for Fun (5)
- Linux Quick Tips (98)
- Linux Tutorials (65)
- Miscellaneous (15)
- Network Tools (6)
- Reviews (2)
- Security (32)
- Smart Home (1)